The results are shown in File Metadata tab:

Course list http://www.c-jump.com/bcc/
Goal: Outline the use of several small, focused modules:
File Type Identification
Extension Mismatch
Interesting Files
Encryption Detection
...and more
What Does It Do?
Determines file type based on signatures
Identifies JPEG based on file starting with 0xffd8
Stores type in database for other modules to use
Why Would You Use It?
More accurately identify type of file
Many modules depend on it
Configuration: None
File-level ingest module
Uses Tika open source library
Detects hundreds of file types and reports them as a MIME type:
application/zip -- audio/mpeg -- image/jpeg
application/octet-stream -> means unknown type
The results are shown in File Metadata tab:

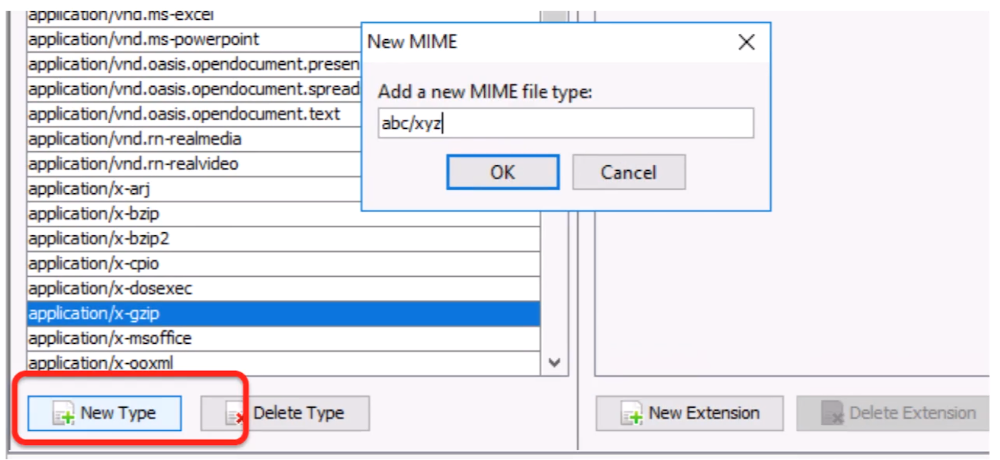
You can define your own file types if Autopsy does not automatically detect them
Tools -> Options -> File Types
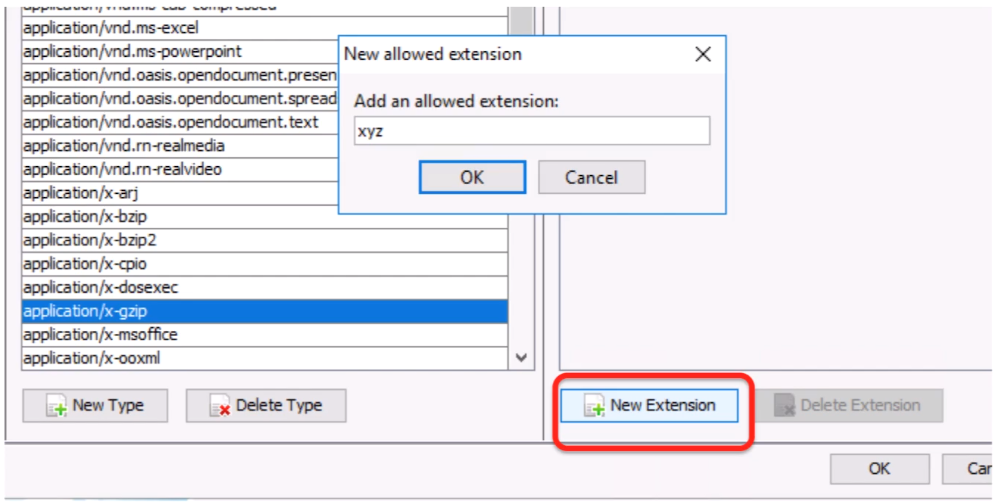
Specify:
MIME Type (you can make one up)
Offset of signature
Signature (in bytes or ASCII string)
If you want to be alerted if the file type is found.

What Does It Do?
Compares file's extension and file type
Flags if extension is not associated with type
Why Would you Use It?
Detect files that someone may be trying to hide
Configuration:
File types to focus on
Skip known files (default: true)
List of extensions for each file type
This module can produce lots of false positives:
Lots of files get renamed to ".tmp" or ".bak"
Lots of files have a ".0" or ".1" extension
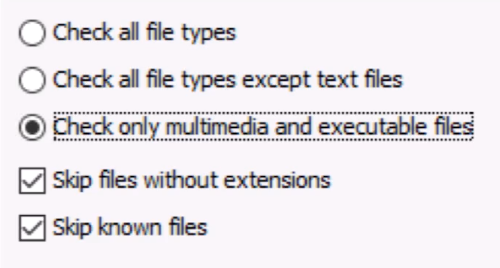
Can reduce false positives by focusing on file types:
Multimedia and executables only are the default:
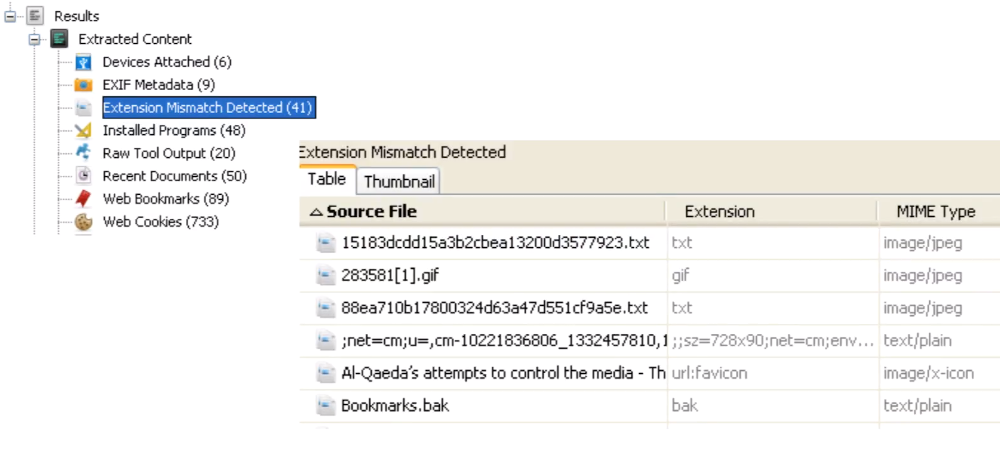
Extension Mismatch results are gathered in Results Tree:
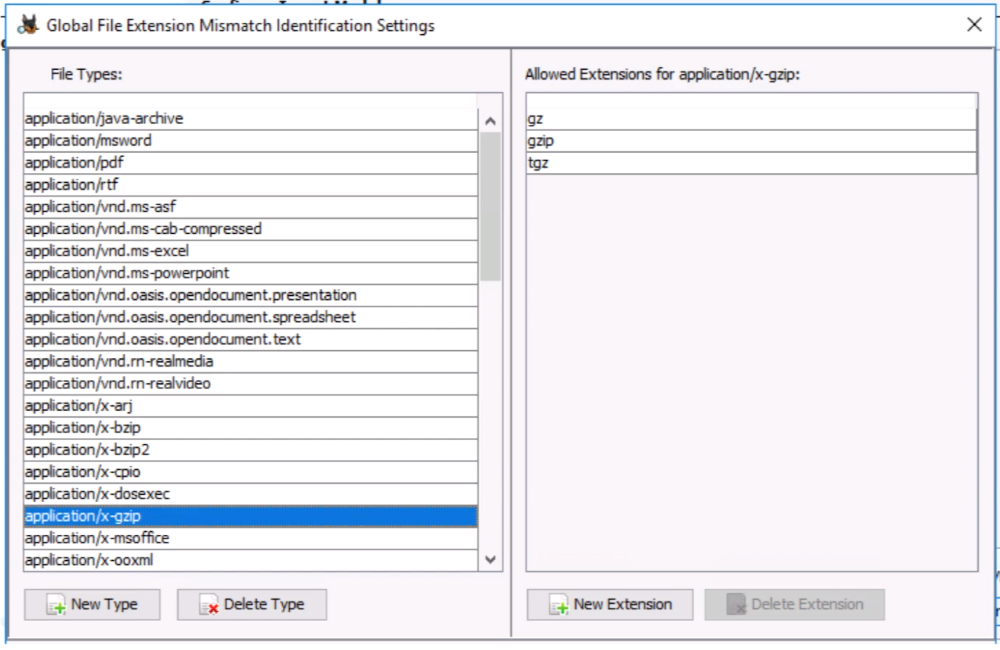
Global File Extension Mismatch Identification Settings:
The system will tell you if it can't detect that type:
What Does It Do?
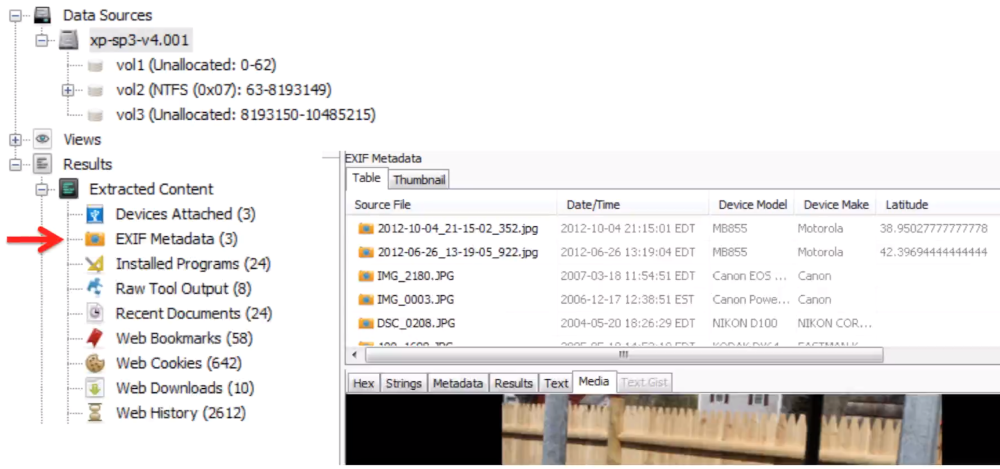
Extracts Exif structure from JPEGs
Stores metadata in blackboard
Why Would you Use It?
Identify camera type used to take picture
Identify time picture was taken
Identify Geo-coordinates where a picture was taken
Configuration: None
Under Results, Extracted Content, EXIF Metadata in the tree:
What Does It Do?
Extracts embedded files so they can be analyzed
Opens ZIP, RAR, and other archive files
Extracts images from Office and PDF files
Why Should You Use It?
To analyze all files on the system
Configuration: None
Extracted files are saved inside of case folder
Added back into the ingest pipelines for analysis
Same priority as the parent file
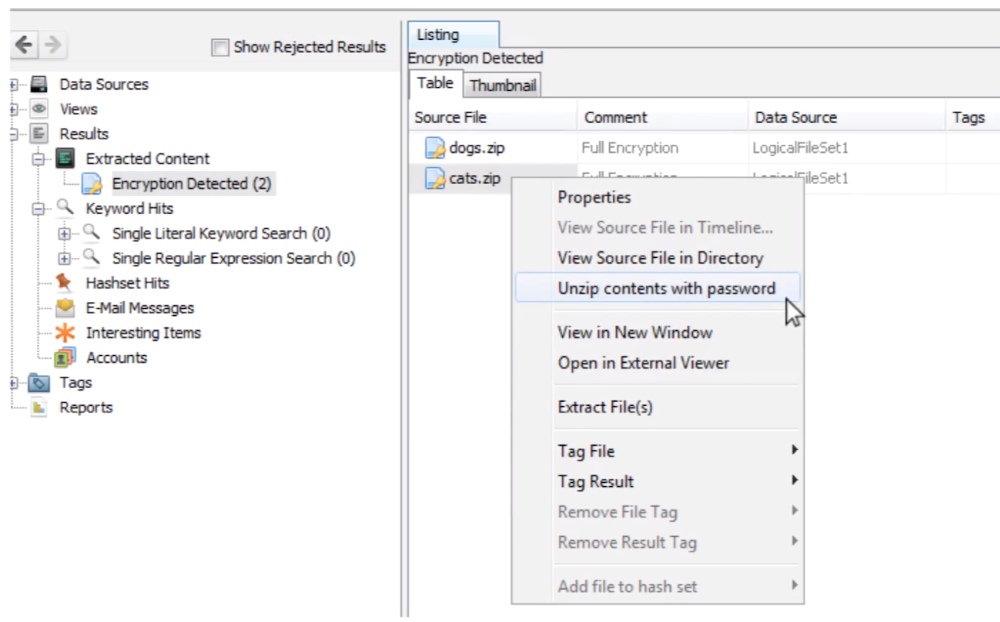
Flagged if it was password protected
|
|
Supply a password by right-clicking on a ZIP file, then open the file:
What Does It Do?
Searches for MBOX, PST, and EML files
Adds email artifacts to blackboard
Adds attachments as children of the messages
Groups them into threads
Why Should You Use It?
Identify email-based communications
Configuration: None
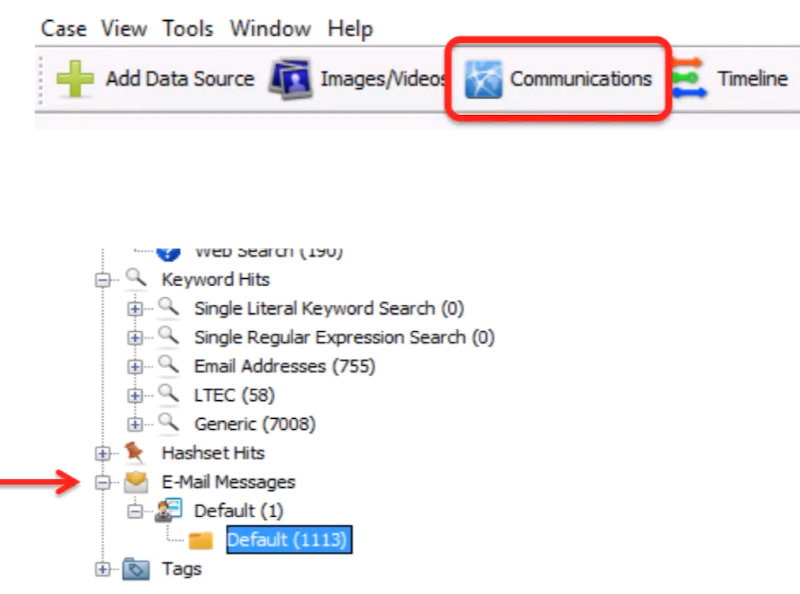
Email results are visible in two places:
Communications Viewer (more on this later), and
in the tree:
What Does It Do?
Flags files and folders that you think are "interesting"
Why Should You Use It?
To always alert and notify when files are found
iPhone backups
VMWare images
BitCoin wallets
Cloud storage clients
You need to make rules for the programs
Rules are organized in the Options panel
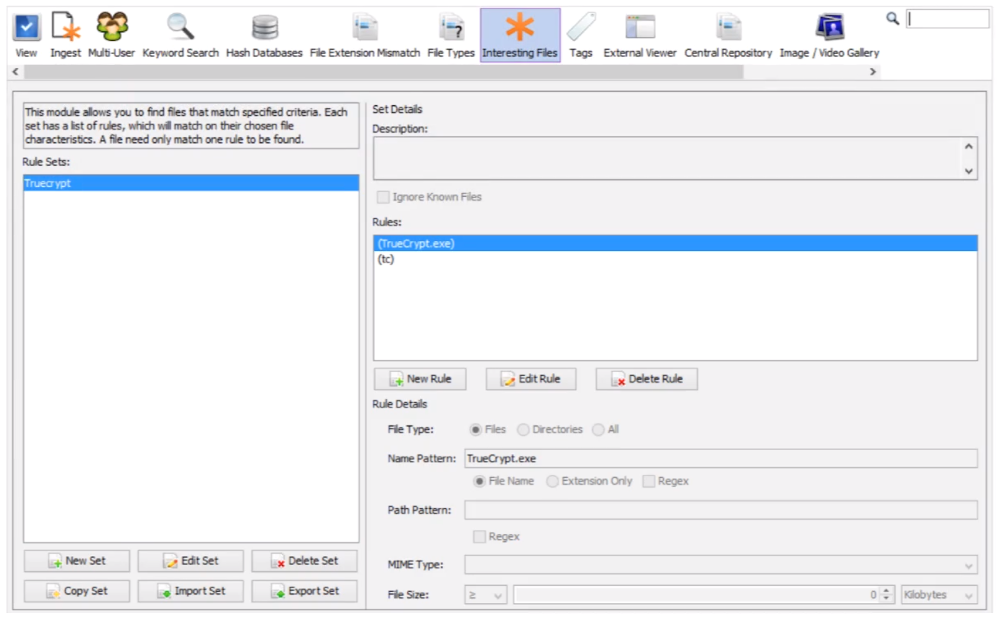
Rules are grouped into sets
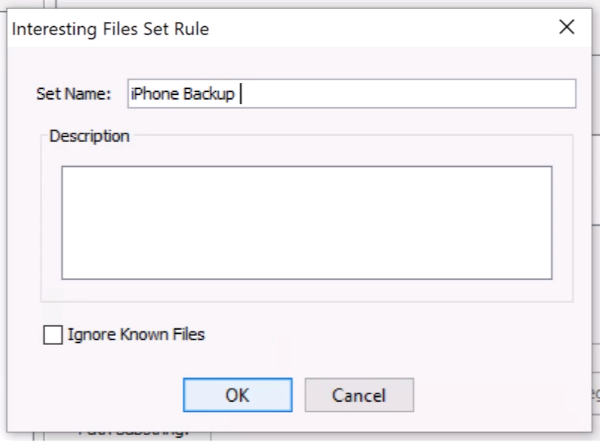
Each set needs a name
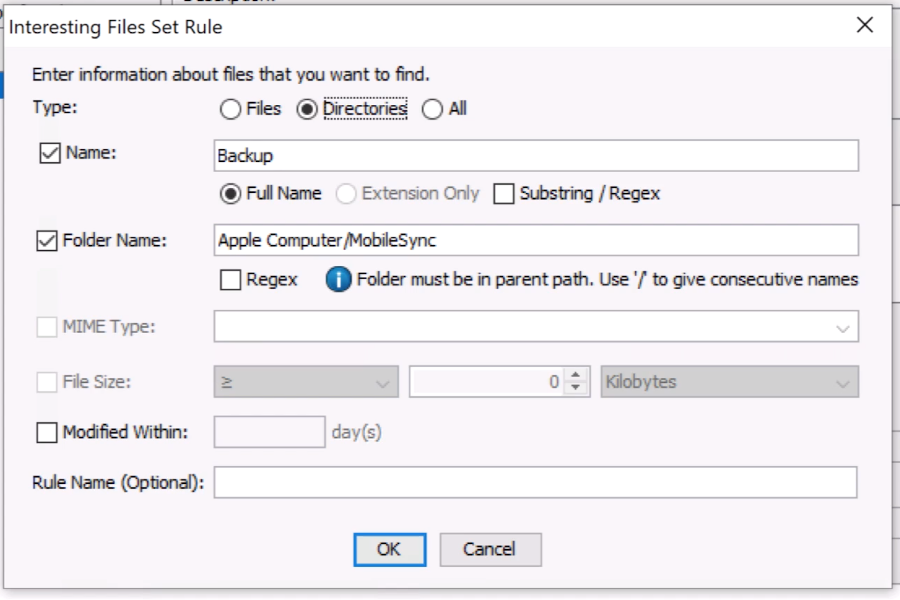
Rules have several optional fields
Type: Match files, directories, or both
Name: Can be full name, only an extension, or a substring/regular expression
Parent Path: Can be a substring (i.e. /Desktop/)
Size
MIME Type
Dates
Set Name: VMWare
Rule 1:
Type: Files
Full Name: vmplayer.exe
Name: Program EXE
Rule 2:
Type: Files
Extension: vmdk
Name: VMDK File
What Does It Do?
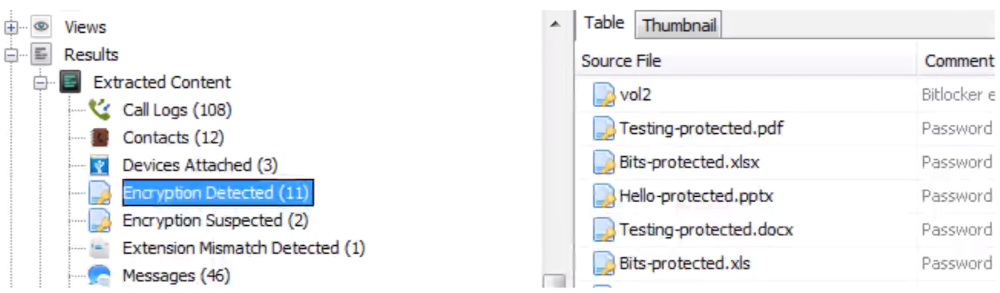
Flags files and volumes that are or could be encrypted.
Why Use It?
Ensure that you are aware of files that may contain additional evidence.
Detects:
Passwords on Office docs and Access DBs.
Possibly encrypted files or volumes:
High entropy (random), multiple of 512 bytes, and no known file type.
Where Do You See Results?
The results are shown in the tree as "detected" versus "suspected":
What Does It Do?
Uses open source Plaso tool to parse various logs and file types to extract out time stamps
Why Use It?
Extract as many dates as possible for the timeline.
Notes:
Some of its time stamps duplicate what Autopsy already extracts.
It can take a considerable amount of time to run, so it is disabled by default.
|
|
What Does It Do?
Analyzes virtual machines found in a data source.
Why Use It?
To process virtual machines that the device's owner may have also used and therefore may contain evidence.
What Does It Do?
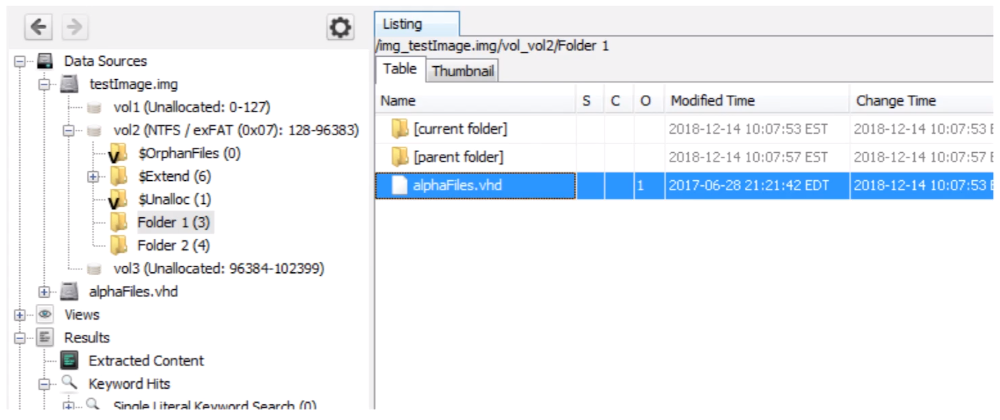
Detects vmdk and vhdi files in a data source
Makes a local copy of them
Reeds them back in as data sources
Configuration: None
New data sources will be added:
What Does It Do?
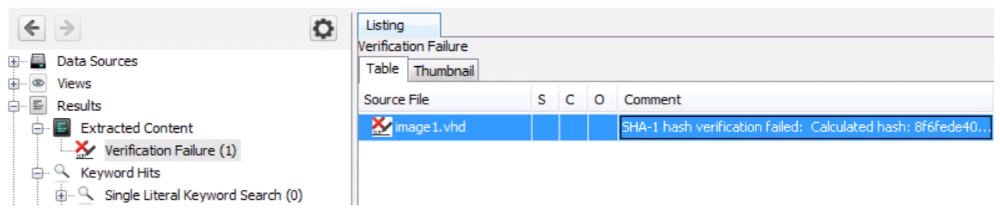
Validates and calculates hash of disk image
Retrieves hash from E01 or what a user entered when data source was added
Calculates current hash
Generates an alert if hashes are different
Saves hash if there was not one already
Why Use It?
Ensure integrity of evidence
The failures of integrity are shown in the tree: